what is SELinux
SELinux is an implementation of a Mandatory Access Control security mechanism. SELinux allows server
admin to define various permissions for all process. It defines the access and
transition rights of every user, application, process and file on the system.
SELinux has three modes:
- permissive(default): The SELinux system prints warnings but does not enforce policy
- enforcing: The SELinux security policy is enforced.
- disable:SELinux is fully disabled. SELinux hooks are disengaged from the kernel and the pseudo-file system is unregistered
Concepts in SELinux:
- Subject: can be taken as process
- Object: can be taken as file/resources
- Policy
- strict: full control, for all daemons
- targeted(default):mainly for network service
- Context(tag being used for access control)
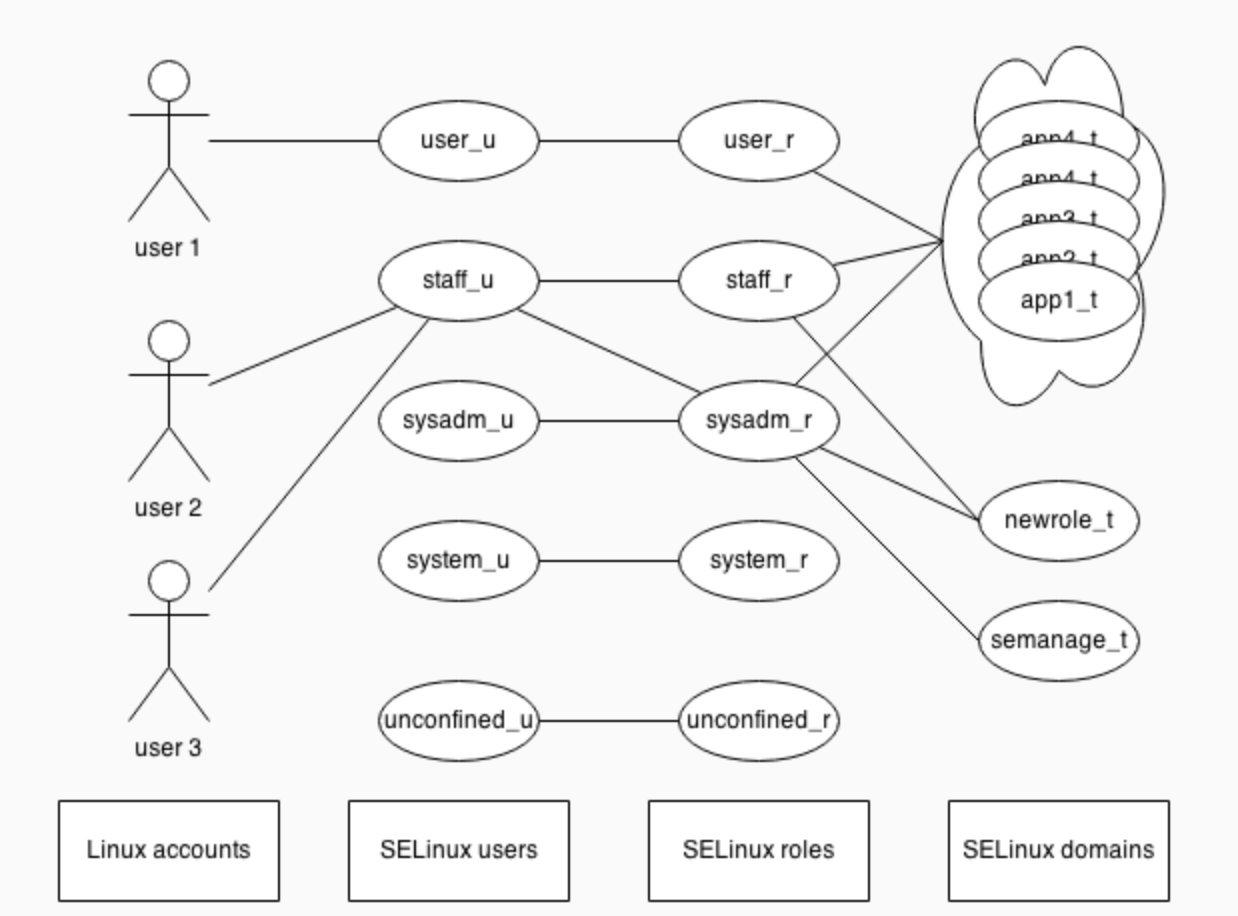
- user: SElinux user, semanage login -l
- role: decide who(SElinux user) can request which domain
- object_r: file/directory
- system_r: programe/user
- type (*most important*): decide which domain can access(read/write) which file/dirctory
- type: file/directory
- domain: programe/user
- sensitivity:[category](Multi-Level Security) (https://wiki.gentoo.org/wiki/SELinux/Tutorials/SELinux_Multi-Level_Security)
How to create a policy:
- using audit2allow, .te is source code, .pp is the module file
 (°0°)
(°0°)
what is AppArmor
AppArmor is an mandatory access control (MAC) like security system for Linux. It is designed to work with standard Unix discretionary access control (DAC) permissions while being easy to use and deploy, by allowing an admin to confine only specific applications.
Basically, it uses profiles to determine what files and permissions the application/process can have.
And it needs other softwares to help to guarantee system security , it’s not a system. Some other softwares are below:
- iptables
- auditd(for log)
- ossec(has a system)
- snort(for network)
- osquery(has a system)
AppArmor has two modes:
- Complaining: profile violations are permitted and logged. Useful for testing and developing new profiles
- Enforced: enforces profile policy as well as logging the violation.
Profiles:
- under folder /etc/apparmor.d, like /etc/apparmor.d/usr.sbin.tcpdump for tcpdump
-
types of rules
Path : this has information on which files the application is allowed to access
Capability: determines the privileges a confined process is allowed to use
Network: determines the connection-type - create options
inherit: create a rule that is denoted by “ix” within the profile, causes the executed binary to inherit permissions from the parent profile
child: create a rule that is denoted by “Cx” with the profile, requires a sub-profile to be created with the parent profile and rules must be separately generated for this child.
deny: create a rule that prepends with “deny” at the start of the line, causes the parents access to the resource be denied. - access controls
r = read
w = write
l = link
k = lock
a = append
ix = inherit = Inherit the parent’s profile.
px = requires a separate profile exists for the application, with environment scrubbing.
Px = requires a separate profile exists for the application, without environment scrubbing.
ux and Ux = Allow execution of an application unconfined, with and without environmental scrubbing. (use with caution if at all).
m = allow executable mapping.
Create profile: using aa-genprof
Limitions:
- limiting to a port is not possible.
- useless to root privileges
- no memory protection
- not a intrusion detection system
what is IDS
references